Iot Hacking And Its Countermeasures
Good day everyone, today i am going to write an article on the topic- Iot (Internet of Things) Hacking. (note: This is going to be long practical guide for IoT hacking as it will cover few of those devices looked and played by me so, get your drinks, popcorn, Netflix ready. Netflix in case you got bored and need some entertainment. This is not a typical guide you will find on internet.) So let us begin, firstly it is necessary to understand “what is an IoT device? The Internet of Things (IoT) is a system of interrelated computing devices, mechanical and digital machines, objects, animals or people that are provided with unique identifiers (UIDs) and the ability to transfer data over a network without requiring human-to-human or human-to-computer interaction. Example includes: smartphones, web servers, smart watches, smart TVs , smart speakers, connected cars, smart home gadgets, network cameras, smart refrigerators , Google home, Google Nest, Amazon Alexa, SCADA systems, ICS systems and many other devices. https://www.softwaretestinghelp.com/iot-devices/
Coming to our next question: How big is Iot thing at this time? Answer is simple- “really big” for instance have a look at the below picture.
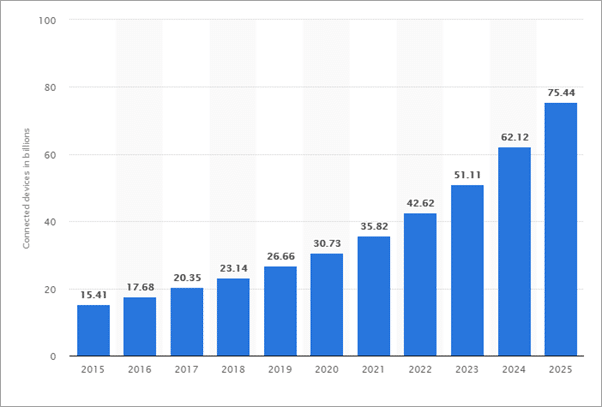
IoT devices were made for user convenience but can also be used for threatening users specially by malicious threat actors. One such example is this news: https://www.news18.com/news/tech/a-couples-nest-smart-home-was-taken-over-by-hackers-and-vulgar-music-was-involved-2321509.html
Now let us discuss advantages and disadvantages of IoT devices:
Advantages of IoT Devices:
- Easy user interaction and GUI environment ( can even be used by non techies).
- IoT possesses strong monitoring feature.
- It provides good automation and control.
- Increased efficiency and time-saving.
- It saves time.
- Automating daily life tasks makes good monitoring of devices.
Disadvantages of IoT Devices:
https://www.peerbits.com/blog/biggest-iot-security-challenges.html
- Internet of Things devices does not have any international compatibility standard (No particular standard compliance).
- IoT devices may get affected by privacy and security breach more easily which may result in devices being used in unethical practices like sending spam emails, etc. Devices can be converted into botnets. Google for more such incidents :)
- Lack of updates for devices specially those operating in critical environments. Example includes SCADA and ICS systems. https://www.zdnet.com/article/scada-security-bad-app-design-could-give-hackers-access-to-industrial-control-systems/
- Use of default credentials (insufficient authentication and authorization)
- Unsafe communication. Many IoT devices don’t encrypt the messages when sending them over the network. This is one of the biggest IoT security challenges out there. https://www.bostonglobe.com/business/2017/03/08/wikileaks-hits-cia-secrecy-software-spying/EQdLVwseMu70HEYlZcowOO/story.html
- Personal information leaks. Experienced cyber criminals can cause massive damage even by finding out internet protocol (IP) address through unsecured IoT devices. These addresses can be used to pinpoint a user’s location and their actual residential address.
- Lack of knowledge/time/money. People either don’t know much about the IoT or don’t care. The lack of knowledge can often be the cause of massive damage to a corporate or personal network. Most people or organizations won’t invest in a secure IoT infrastructure because they find it too time-consuming or too expensive.
- RFID Skimming. This is the type of skimming where hackers intercept the wireless information and data from RFID chips used on debit cards, credit cards, ID cards/passports, and other documents. Hackers use NFC-supported devices that record all the unencrypted data from the RFID chips and then broadcast through wireless signals.
Get more detailed reports here: https://www.ubuntupit.com/25-most-common-iot-security-threats-in-an-increasingly-connected-world/
How to deal with IoT devices security issues?
- Perform vulnerability testing on a regular basis. Companies should release safety advisories and guidelines from time to time to spread awareness among consumers. They can also launch bug bounty programs for their various IoT devices present. Users are advised to regularly change their login password and username to prevent unethical minded people to violate their privacy and never use default credentials in their login pages. https://www.cbronline.com/news/iot-bug-bounties
- Vulnerabilities to watch out for. These include the standard vulnerabilities of missing patches and weak passwords, but dig in deeper and ensure that IoT systems are using Transport Layer Security to encrypt communication sessions and encrypt data at rest, as well as making sure devices are not susceptible to denial-of-service attacks. OWASP IoT Project is of great use here. https://www.owasp.org/index.php/OWASP_Internet_of_Things_Project
- Document your findings. Carefully watch recently discovered vulnerabilities in your system and act accordingly.

Now let’s go for the most interesting thing, the thing for which we all are here (IoT hacking) :}
Before getting started in IoT device hacking we need to get familiar with one more thing that is shodan. Shodan is a search engine that lets the user find specific types of computers (webcams, routers, servers, etc.) connected to the internet using a variety of filters. Some have also described it as a search engine of service banners, which are metadata that the server sends back to the client. This can be information about the server software, what options the service supports, a welcome message or anything else that the client can find out before interacting with the server. https://en.wikipedia.org/wiki/Shodan_(website)

Few resources to get started: https://www.cpomagazine.com/cyber-security/5-simple-iot-devices-that-can-become-entry-points-for-hackers/
Let’s get started now (finally we are inn.. 😉)
I typed “satellite communication shodan” on google.com and press enter. We will come across a variety of satellite connected IoT devices 😈.

Now click on any of those links (as shown in the screenshot above) and you will come across a wide list of such IoT devices listed by shodan over the internet. I opened Satellite Receiver Web Interface page link and came up with many devices around the world.

And the best thing about these devices is that you don’t really need any authentication for reading such a critical information. It can be accomplished by just clicking and viewing those random devices. Also we can take help of Google here to search for default user login credentials for devices.

As you can also see data received from different satellites such as GLONASS, GALILEO, Oscillator, SBAS, GPS. In the Left corner of the image we can also see other status of this device but covering all that will result in making this blog post more lengthy :( . Antenna shows the current status of antenna, company name, position, other sensitive information. Message log shows all the errors and successful connection established by this device from satellite. Position shows the current geographical location and other coordinates of the device.
Local time: 08:23:39.0 Position latency: 0.03 s Latitude: 52º 56' 24.66482" North Longitude: 70º 12' 42.37332" East Ellipsoidal height: 393.283 m X: 1304152.050 m Y: 3624757.904 m Z: 5066848.535 m HDOP: 0.7 VDOP: 1.1 GDOP: 1.5 PDOP: 1.3 Position quality: 0.547 m Height quality: 0.837 m
Reference Position Latitude: 52º 56' 24.63728" North Longitude: 70º 12' 42.36694" East Ellipsoidal height: 396.626 m X: 1304153.074 m Y: 3624760.399 m Z: 5066850.690 m
Now moving towards our next IoT device (I won’t be repeating the same process again of searching and narrowing down shodan results. You need to do that on your own. Information shared till now is more than sufficient).
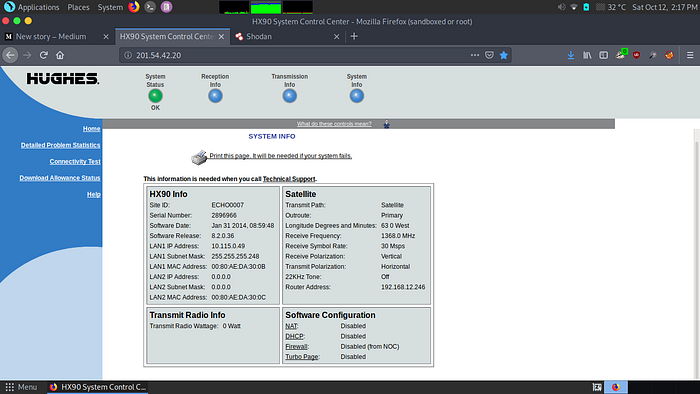
Here is another satellite communication system indexed by shodan and is available without any login credentials. However this device ain’t of much use but you can view the information that is being shared and received by this device. This is a critical issue as it is a case of sensitive system information disclosure.
Another device:
Moving forward to another IoT device here is Tandberg television web server. Used shodan query: “Tandberg Television Web server”. Again all of these devices are available to access without any user login credentials which is very bad here 💁 #noprivacy . User here even put his email address.

All these devices are really noobish on earth and anyone can “hack into” them easily. Even a script kiddies can do that without any efforts :{
Yet another device:
This device is a ICS system(Server: SOLAR controls product server) from Olomouc,Czech Republic that was too easy to hack even for a script kiddie too (again the same thing). Let’s move ahead now. This was also found to be easily exploitable.https://www.shodan.io/host/94.124.107.213 . This is a probably a solar panel control web interface in a solar farm.

You can find similar web interface panels and other critical solar infrastructures using similar shodan query.
Just another critical device: (read electricity?)
By using shodan query we came up a power grid by Schneider Electric in Westport city of United States managed by Frontier Communications. https://www.shodan.io/host/32.219.104.125 . This was also an easy find like other devices “be it in isolation or in crowded”. In this we can read electricity transmission as you can see below.

Other interesting findings are:
>Revenue Measurements.
> Power Quality.

Next device please:
Our next target is Web-based Management system located in Apo city of United States hosted by ISP Telemar s.p.a. https://www.shodan.io/host/46.229.85.155 . This is a SCADA system accessible easily to anyone be it evil minded. It requires as such no interaction to read data transmission which violates basic privacy principles. Wait. What? Privacy in SCADA? 😆 .
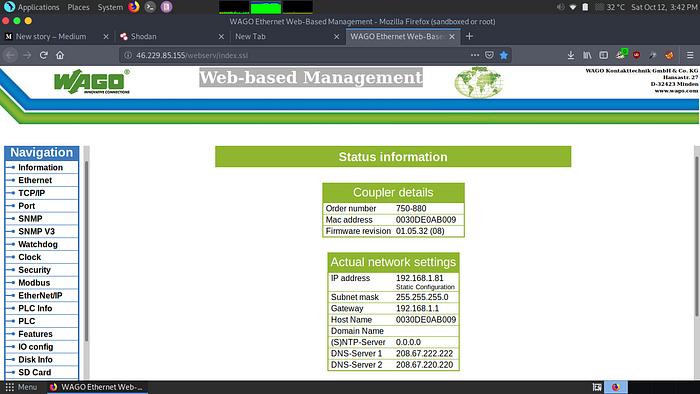
Here you should focus on the information available for users to read. It was also an easy exploitation. They should also launch a bug bounty program for their IoT devices. This is the time. Remember cyber command wing of USA Government ? We don’t have bad intentions am i right?
Solar Inverter IoT device:
Our next target was solar power grid inverter from Hunfeld city of Germany hosted by ISP Unitymedia. https://www.shodan.io/host/176.198.61.219 . This was again a noobish target as it required no authentication and allowed anonymous users to make changes and read transmitting data.

By clicking on “DOWN” button it allowed us to downgrade the electricity transferred by this power grid. Sounds dangerous right? 😐. Other options enabled us to perform a good cyber attack on this power grid however we stopped here. #ethics .

Another similar thing is that we were able to read the amount of electricity produced by this particular grid. We were also able to read event logs of this grid. This is really risky and scary part but also a bitter truth on the other hand.
Just another product of today:
Another IoT device was from United Kingdom managed and owned by Vodafone Broadband . https://www.shodan.io/host/84.9.126.138 . This is another ICS system.

This also required no authentication to view and make changes to this server. What we think is that it is a local wireless internet providing server.

This can be a dangerous case when accessed by malicious threat actors. Even a noob ca access this one. Feels sad though.
How many more devices dude?
This time we hacked a hotel room web interface of a hotel in Boardman city of United States hosted by ISP Amazon.com. We were able to access user profiles, increased room thermostat temperature remotely, got all the hotel booking information that too without any authentication :) https://www.shodan.io/host/52.33.247.163

OK this is last one promise:
This time we were able to hack into a train messaging system’s web interface located in Grants city of United States hosted by ISP Swc Telesolutions. https://www.shodan.io/host/199.115.129.9

We were able to successfully read warnings and messages transferred through this system. Some of it you can see in the above screenshot as well. Below is the list of all those trains that are recorded by this message box.

Below is the detailed list of trains. Includes train number, etc information.

Ending notes:
“We need to get smarter about hardware and software innovation in order to get the most value from the emerging Internet of Things.” — Henry Samueli
